Потеря домашнего питомца влечет за собой не только эмоциональную боль, но и необходимость принятия
Пункты приёма металлолома играют важную роль в экономических и экологических аспектах современного общества.
Продвижение на YouTube является ключевым аспектом успеха любого видеоблогера или компании, стремящихся увеличить свою
Изготавливаются эти шкафы из высококачественной стали, что гарантирует их долговечность и устойчивость к внешним
Выбор мебельной ткани - это не только вопрос дизайна, но и практичности. Мебельная ткань
Технический перевод играет ключевую роль в глобализированном мире, где научные и технологические достижения быстро
В современном мире, где технологии проникают в каждую сферу жизни, онлайн-помощь студентам становится все
Корпоративное обучение английскому с носителем языка открывает новые возможности для компаний, стремящихся к глобализации
Выбор компании для поверки счетчиков воды должен основываться на комплексном подходе, включающем оценку всех
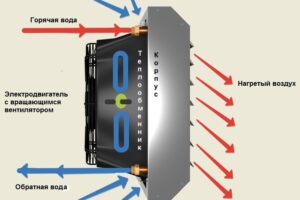
Тепловентиляторы являются универсальным и доступным решением для обогрева, которое сочетает в себе удобство, эффективность
Топливные карты становятся неотъемлемым инструментом для бизнеса, особенно в сфере транспорта и логистики.
Посещение парикмахерской для многих детей – это не только процедура по уходу за волосами,
Шансон - это не просто музыкальный жанр, это целая культура, отражающая жизненные реалии, чувства
Аттракционы не только приносят радость и улучшают настроение, но также могут оказывать положительное влияние
Туры на праздники стали популярным выбором для тех, кто хочет особенно отметить значимые даты
8 Марта – это не только повод поздравить женщин с их праздником, но и
Процесс создания архитектурного макета включает несколько этапов: от разработки концепции до детальной проработки и
От изысканных обручальных колец до модных аксессуаров, каждое кольцо несёт в себе определённое значение
С помощью алгоритмов машинного обучения искусственный интеллект способен генерировать изображения, которые могут варьироваться от
Бассейн что означает во сне? Толкования сонников объяснят, к чему снится Бассейн женщине или
Сны с воскресенья на понедельник в большинстве своем не очень выдающиеся. Но если сюжеты
Часто кто-то жалуется, что ему снится один и тот же человек каждый день. Вроде
История происхождения сонников, самые популярные издания. Сонник Ольги Смуровой: толкование снов, стадии сновидений и
Сны об украшениях с драгоценными камнями предвещают только самое хорошее: крепкое здоровье, судьбоносное знакомство,
Хотите узнать к чему снится Зерно во сне? Смотрите что значит, если видишь
Толкование снов женщины, когда снится зеленый виноград. К чему снятся виноградные грозди другого цвета
Подробная интерпретация сновидения про перо лука. Во сне оно часто предсказывает слезы и огорчения,